Author: Andrés Rieznik
Senior Researcher
@AndresRieznik
Scientific research on hackers motivation: a case study

Knowing the threat landscape is essential for the implementation of efficient cybersecurity strategies. Most people, including security professionals, get their ideas about the world from news that viralize in social media. As it is common knowledge now, this leads to biases and distortions. With increasing attention from news outlets, cybercrime is not an exception. As a result, common perceptions about hackers behaviour and motivation may be greatly distorted.
But, how can the motivation of cyber attackers be formally study? Common approaches include, forensic analysis and surveys on incidents trends. One recent study from Cambridge University has approached this question differently, using the gold standard in behavioral science: randomized controlled trials. The results are both interesting and naive. First, let's go to the naive part.
Alexander Vetterl is a postdoc researcher working in the Cambridge Cybercrime Centre at the Department of Computer Science and Technology. He recently finished his PhD with a thesis titled “Honeypots in the age of universal attacks and the Internet of Things”. A honeypot is any monitored vulnerable element in a computer system set up as a decoy, mimicking potential targets for attackers. For example, a computer with the password “1234” may be added to our network so hackers will easily intrud. Once the hacker is in, his behaviour can be tracked,and his motivations assessed. Honeypots can run on real-hardware machines or on virtual machines.
As part of his PhD research, Dr. Vetterl and his colleagues set up a series of virtual honeypots using 50 IPv4 addresses that belong to the University of Cambridge. They deployed the honeypots for a period of 365 days (October 26, 2017 to October 25, 2018). The target computers were set up with a standard Linux Ubuntu operating system. To gain access to them, trespassers had to break into them successfully through Internet-wide scanning and guessing the authentication credentials. Researchers set up ten credentials for legitimate users with common username/password combinations such as admin/admin, root/123456 and raspberry/pi.
In order to study the prevalence of human trespassers, they supplemented the password authentication with a CAPTCHA. The CAPTCHA allowed researchers to distinguish between humans and bots as the latter should not be able to solve it. And, to better understand the motivation and psychological traits of system trespassers, they designed a survey which was aimed at those that attempt to access University computers without legitimate access. After the CAPTCHA was solved, they presented a welcome message. Then, they told the attacker that he had logged into a honeypot and asked him to take part in a survey containing 44 questions. This is the message the attachers received:
You have gained access to a computer system we run for research purposes and we do not think we have authorised you to do that. We, academic researchers from the Computer Laboratory, University of Cambridge, aim to understand why you have chosen to access our computer system and your views about unauthorised access more generally. We will also be asking you some questions about your personality which may provide some insights into your personality type. As you may find this personal insights especially interesting, we will provide results at the end of the survey!
This is your opportunity to tell us your side of the story and it will allow you to learn more about your personality and strengths! In order to get started with the survey, please go to: (link address).
Your response will be immediately de-identified upon receipt and, of course, we do not intend to expose you or disclose illegal behavior. We will keep your responses strictly confidential. ¡We really welcome your feedback!
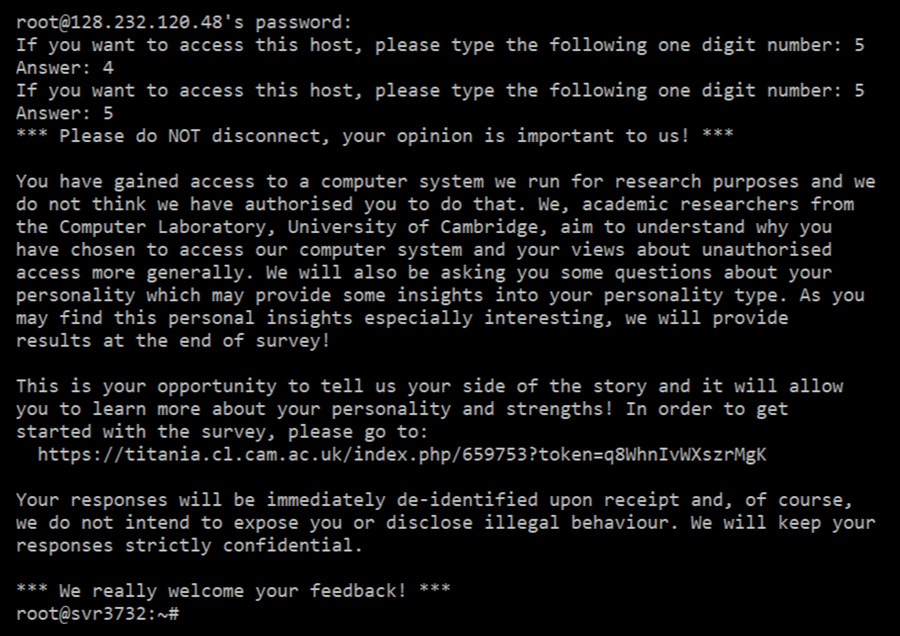
Of course, this is the naive part, and, of course, they obtained not any single answer. Zero. As Dr. Vetterl wrote in his thesis,
“Unfortunately, only 4 of the 99 individuals to whom we showed the welcome message, used the URL to view the survey and none of them completed the survey”.
We think of this bizarre hope of cooperation from cyber criminals in exchange for a result from a psychological test as anecdotal evidence that the shift in hackers motivations during the last years has not been yet fully internalized by researchers and the cyber community more generally. “This is your opportunity to tell us your side of the story and it will allow you to learn more about your personality and strengths!”
It is true that during the early days of the Internet, the majority of attackers were motivated by peer recognition, or curiosity. Maybe in those days some hackers would be motivated to interact with researchers from prestigious academic institutions such as Cambridge University. In the last years, however, financial motives have moved to the foreground as shown by a large body of literature [references].
As we see it at BitTrap, the prevalence of blockchain (Bitcoin, Ethereum, etc.) in the last decade accelerated the professionalization and diversification of the attacker. They’re analyzing their operations, making adjustments and optimizing their business. There is an easily accessible retail market of malware tools, which includes client support and maintenance services from cybercrime organizations. As with any other resources, ransomware technology is a commodity now available on the black market. The threshold for entering the game is lower than ever (hackers even compete against other hackers to first reach and lock vulnerable systems).
Take the Colonial’s network case as an example. These were clearly inexperienced attackers looking to monetize their intrusion. As CNN reported: “(...) there are indications the individual actors that attacked Colonial, in conjunction with DarkSide, may have been inexperienced or novice hackers, rather than well-seasoned professionals, according to three sources familiar with the Colonial investigation.”
Let's now go to what is, in our opinion, the most interesting parts in Dr. Vetterl studies.
Since they added a CAPCHA to their experimental paradigm, they were able to estimate the proportion of bots and humans. Their findings? “The predominant attacks rely on Internet-wide scanning for device discovery. (...) The number of human trespassers is orders of magnitude lower than previously assumed, and that previous research measured the behaviour of automated scripts. These scripts are only programmed to evaluate the systems' usefulness by looking for a predefined set of characters such as indications of a shell prompt”
This is the first time, to the best of our knowledge, that a scientific publication acknowledges what many in the industry know: the cybercriminal landscape experienced profound changes in the last decade and the common public perception of hackers' motivation is misleading: notwithstanding the existence of a minority of state sponsored actors, the majority of attacks are no longer politically or ideologically motivated but instead look for easily and efficient monetization strategies.
Although there is a diverse population of attackers with different skill levels and resources, motivation is one of the key elements that can help describe their behavior.
Understanding how attackers relate to your infrastructure through the attack lifecycle can help plan and optimize some strategic decisions.

